DDoS Attacks - What Are They and What Impact Do They Have?
DDoS Attacks - What Are They and What Impact Do They Have?
Denial-of-Service (DOS) & Distributed Denial-of-Service (DDOS) attacks focus on attacking a network with the intention of rendering it difficult or impossible for normal use.
These attacks flood servers, systems or networks by overloading it with useless traffic. Whilst a server crash can often be solved via a reboot, flooding attacks can be more troublesome to resolve.
We will not be including links to any of the DDOS software mentioned below as we do not condone their use.
DOS Vs DDOS
The difference between DOS & DDOS is fairly substantial. A DOS attack is when the attacker uses a single internet connection to carry out the attack. This is usually with the intent to flood a target with fake requests. The aim here is to exhaust resources at the opposite end, i.e. RAM / CPU.
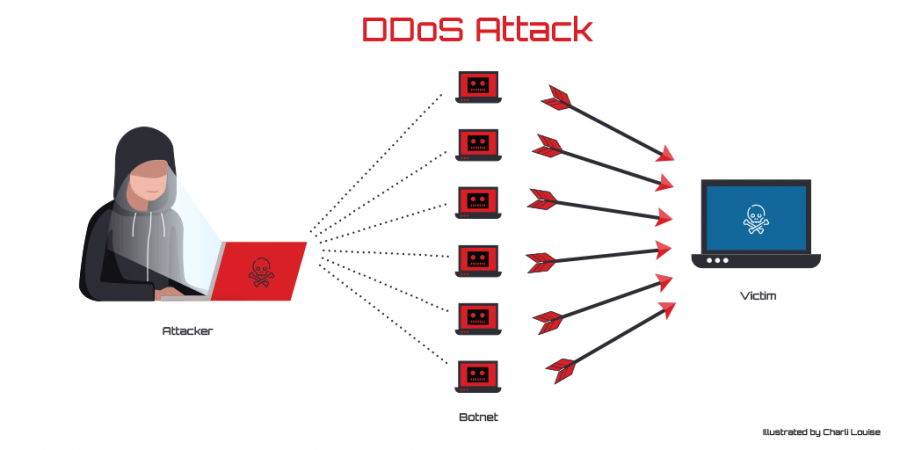
DDOS attacks, however, are instigated by multiple connected devices. These are substantially harder to deflect due to the sheer number of devices involved. The computers behind a DDOS attack can be scattered around the world, making tracking the original source almost impossible.
How are these executed?
DOS attacks are, generally speaking, launched from DOS tools. many of these can be found instantly through a Google search (XOLC, HULK, R-U-Dead-Yet.) These can be easily accessed and used by virtually anyone. In some cases, DOS attacks are carried out using home-brewed scripts created independently by hackers. Although they still carry out the same/similar effect.
DDOS attacks are launched from "Botnets", a network of private computers infected with malware. These remote consoles are then directly controlled by the attacker.
Signs You are the Victim of an Attack
Depending on your level of awareness, you may not notice the initial signs of a DOS/DDOS until it's happened. Things to look out for include:
Everyone experiences bad network performance from time to time. The length of time is the important factor, If the service is slowed or down for more than a day it could indicate a DOS attack.
Why are these attacks carried out?
There can be multiple motivations behind DOS/DDOS attacks. Whilst it's possible that you could be targeted for a number of reasons, based upon your brand and industry, it is likely you can pinpoint which you are likely to experience, below are the three most known:
Extortion is a well-known motivator and has become a more prevalent method as hacker scripts and tools are evolving. Using a DOS/DDOS attack for extortion involves the attacker demanding money in exchange for halting a detrimental attack. Sites like Bit.ly, Vimeo & Meetup have received several extortion notes in the past.
Hacktivism is when an attack is carried out for a political or social purpose. The most known of recent years is the group Anonymous who were responsible for the cyber attacks on ISIS. Generally speaking, unless your website contains or is promoting material it shouldn't be, you won't be on a hacktivists radar.
Small/medium businesses are likely to experience competition fuelled attacks above the others. These attacks can have different goals. One of the main outcomes to achieve is to cause substantial disruption, so the customer diverts to a competitor (i.e. the person who ran the attack) at the same time this would also cause substantial financial damage.
Another goal could be to prevent a competitor from taking part in an important event. This can vary depending on what industry your business is in, for example, Cyber Monday. In a more radical case, the end goal could simply be to shut down the target site for weeks or even months.
The main focal point of the attacks is the costs inflicted. How much money do you lose if you're a victim? The figure for this will vary heavily on how big your business is & how heavily you rely on online sales. I.e. if you get substantial traffic regularly it will have more of an impact on you than someone who doesn't. It's been found that on average, a DDOS attack can cause a business £40,000 per hour. Reputation, however, is equally important. The overall perception of your brand is likely to plummet if you're seen as vulnerable. This can then lead to fewer sales in the future and a further loss of profits.
How can you defend against an attack?
You cannot 100% prevent an attack. You may never even experience one, but it's important to understand what precautions you can take in order to deter an attacker and/or respond to an incoming attack.
Incident Response – An incidence response is used to address and manage the subsequent damage from a breach or attack. The response is in place to minimise the damage and reduce the overall costs that come with recovery as well as other collateral damage, such as brand reputation.
Organisations should have a clear incident response plan in place that defines what an incident is & provides a clear guided process to follow when one occurs. This also includes specifying what employees, teams or individuals are responsible for managing each of these tasks.
Bandwidth over-subscription – This involves leasing a significantly larger capacity of bandwidth than you actually need. This is usually the case with large businesses, so this may not always be an applicable step. Leasing a much larger capacity is usually to account for the growth of the business following a recent marketing campaign; however, this also acts as a buffer for a DDOS attack.
Whilst it's highly unlikely that increasing your width by 100-500% will stop an attack, it will provide you with extra time to react. The defence here comes from the resources available at the attacking end; if the attacker cannot muster enough traffic to overwhelm the extra capacity then a volumetric attack is ineffective.
Third Party Service – Regardless of the size of your business, if you're hit by a 200 Gbps attack directly, you will suffer the consequences. Larger businesses usually implement a BGP or DNS based redirect service in order to protect themselves in case they are victim to a sustained attack.
CDN (Content Delivery Networks) – A CDN can act as another “barrier” when dealing with an attack. A CDN delivers pages and web content to a user based on their geographic location through the use of distributed servers. Whilst this is definitely far from a solution, the attack will have to go through these servers before directly hitting yours, giving you more time to prepare/react.
There are many other protocols you can put in place to prepare for an attack. With hackers getting smarter and more ambitious by the day it's virtually impossible to know what will be the most beneficial. Maintaining a strong awareness is the easiest yet strongest method of preparation.
Anyone can be the victim of an attack. Would you be able to survive a £40k per hour attack? It's easy to prepare for an attack yet many businesses apply the “it won't happen to me” mentality and before you know it their business has collapsed. Take the time to prepare your business.
Website Security is becoming increasingly important. Ensuring your website is secure is the first step in preparing yourself for possible attacks. However, Google's upcoming update will start affecting unsecured websites. We have an article covering everything you need to know here . We offer a Cloud Flare integration service to enable website security.
As a CDN Cloud Flare also provides a base defence against the attacks listed above. Get in touch with us on 01332 477575 or email Admin@devmac.co.uk to talk about making your website secure.






